In our last post we introduced you to APT3 and promised to identify the individuals behind the intrusion. Today we will follow the trail left by APT3’s infrastructure procurers and will identify our first APT3 operator, Mr Wu.
Mr Wu
The trail starts in 2010, when FireEye researchers analysing the Pirpi backdoor used by APT3 identified a sample that communicated with the domain twadcorp[.]com. WHOIS information from late 2009 for this domain gives a registrant name: “Mr Wu”.

From APT3 to mxmtmw
To continue the investigation, we need to examine a second Pirpi sample, this time one that communicates with the domain grayflag[.]net. WHOIS information for the domain from 2009 gives the email address mxmtmw[at]gmail.com.

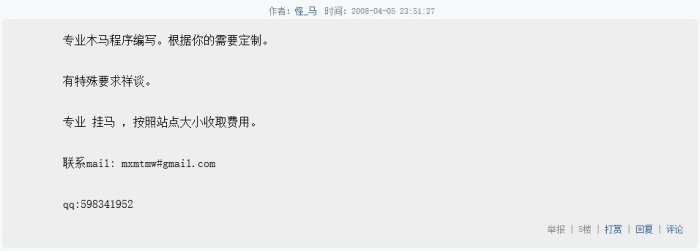
Luckily for us, the string “mxmtmw” is fairly unique online and has also appeared elsewhere, including in a group called Ph4nt0m in 2008, a year before the Mr Wu registration entry for twadcorp[.]com above. In one of those posts the mxmtmw string was used as the username of a poster, part of whose email address is visible in the archives as wuyin…[at]gmail.com.
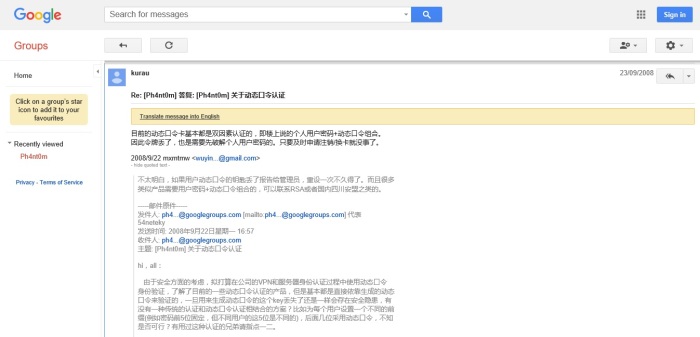
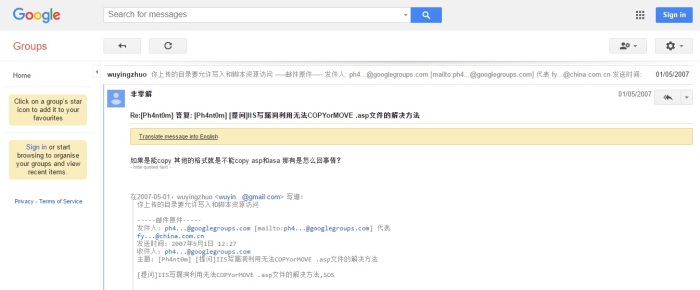
Two further domain name records can be used to confirm Yingzhuo as Mr Wu’s given name.
Returning to the mxmtmw e-mail address, it also briefly appeared in registration data in mid-2011 for the domain grayhat[.]cn. Another e-mail address that was associated with the same domain (it appeared both before and after mxmtmw in the data) is wyz5678[at]163.net. “wyz” possibly stands for “wuyingzhuo”, the name we found in Google Groups.
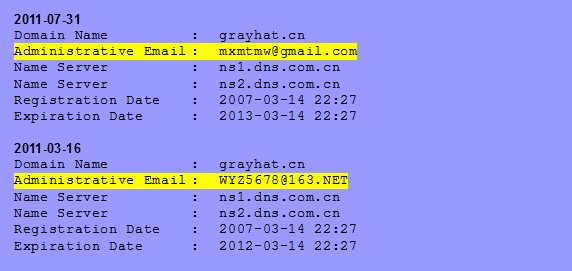
The wyz5678 e-mail address also appears in registration information for another domain-name: ciscocorp[.]com which may lead us to a possible location for APT3.
Infrastructure in Guangdong, China
DNS analysis of the ciscocorp domain shows that ssl3.ciscocorp[.]com previously resolved to IP address 59.42.254[.]195. That IP is owned by “guangdong guangxin tongxin fuwu you”, which translates into English as the “Guangdong Guanxin Communications Services Company”, a wireless telecommunications services company in Guangdong, China. This is possibly an ISP used by APT3 and may give some clue as to the location of the group.

As shown above, similar sub-domains of two other domain names – httb[.]net and caelate[.]com – have also previously resolved to the same IP address. This is significant because the registered name in 2011 for both domains was “yingzhuo wu”.

In summary, it is possible to follow domain name registration data from APT3 tools and domains to Wu Yingzhuo. Wu Yingzhuo might live or work in Guangdong, China, and has expressed an interest online in Trojan development.
We intend to continue the trail from httb[.]net and to introduce you to a second member of APT3. Read our next post for more truth behind this intrusion.
2 thoughts on “Who is Mr Wu?”
Comments are closed.